INFORMATION COMMUNICATION TECHNOLOGY (Theory)
July 2017
THE KENYA NATIONAL EXAMINATIONS COUNCIL
DIPLOMA IN SALES AND MARKETING
DIPLOMA IN SUPPLY CHAIN MANAGEMENT
DIPLOMA IN BUSINESS MANAGEMENT
DIPLOMA IN COOPERATIVE MANAGEMENT
DIPLOMA IN HUMAN RESOURCE MANAGEMENT
DIPLOMA IN ROADS TRANSPORT MANAGEMENT
DIPLOMA IN TOURISM MANAGEMENT
DIPLOMA IN TOUR GUIDING MANAGEMENT
DIPLOMA IN PETROLEUM MANAGEMENT
DIPLOMA IN PROJECT MANAGEMENT
DIPLOMA IN INVESTMENT MANAGEMENT
DIPLOMA IN MARITIME TRANSPORT LOGISTICS
DIPLOMA IN HUMAN RESOURCE MANAGEMENT
DIPLOMA IN DISASTER MANAGEMENT
MODULE I
INFORMATION COMMUNICATION TECHNOLOGY (Theory)
Paper 1
1. (a) (i) Explain the term computer network as used in information communication technology. (1 mark)
(ii) Explain two circumstances where a switch could be preferred over a hub while networking computer systems. (4 marks)
(b) Commlink Enterprises has set up an Internet connection to support its business transactions. Explain three ways the enterprise could benefit from this connection. (6 marks)
(c) Distinguish between multi-tasking and time sharing odes of data processing. (4 marks)
2. (a) Jared used format painter feature while editing a word processing document. Outline two advantages of using this feature. (2 marks)
(b) (i) A systems administrator intends to secure a workbook against unauthorized manipulation by other users. Explain two methods that he could use to achieve his objective. (4 marks)
(ii) Table 1.
Shows a worksheet extract of commission earned by sales persons in four quarters for the year 2014. Use it to answer the questions that follow.
Table 1
I. Using cell references only, write a formula that could he used to calculate total commission for Mary over the year. (2 marks)
II. Using the COUNTIF function, write the function that could he used to display the number of salespersons who earned a total commission above 1(sh. 50,000. (2 marks)
(c) Ken has been contracted by Mauzo Company Ltd. to conduct a security audit on its database. Outline three threats that he could identify during the audit. (3 marks)
(d) Explain a circumstance where direct file access method could be used in a company information system (2 marks)
3. (a) Explain the function of each of the following features in a presentation program:
(i) Duplicate;
(ii) Comment. (3 marks)
(b) Handouts arc commonly used during printing of presentations. Explain one advantage that could be influencing the choice of this feature. (2 marks)
(c) Mishoni institute intends to interconnect its live campuses located in different countries. Describe the appropriate type of network they could use. (4 marks)
(d) Explain three security measures that can be used in an organization while browsing internet. (6 marks)
4. (a) (i) Differentiate between analog and digital computers. (4 marks)
(ii) Joel intends to use a master slide to create his presentation. Explain two advantages he could realize from the use of this tool . (4 marks)
(b) Explain the circumstance under which each of the following input devices could be used in a supermarket:
(i) Keyboard;
(ii) Magnetic card input. (4 marks)
(c) Outline three positive effects of using ICT in marketing to an organization. (3 marks)
5. (a) (i) Allan intends to insert a picture into a slide. State two sources he could get this picture from. (2 marks)
(ii) Outline three functions of computers in a business environment. (3 marks)
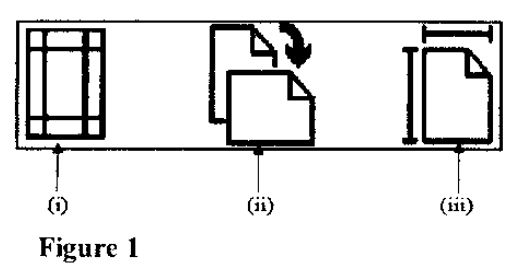
(b) Figure 1 shows tools used in a word processing program. Explain the function of each of the tools labelled (i), (ii) and (iii). (6 marks)
Figure 1
(c) Joseph would like to input a table in a word processing document. Explain two ways he could achieve this. (4 marks)
6. (a) Mourice has been requested to acquire an operating system for his organization. Explain three factors other than cost, he could consider. (6 marks)
(b) Outline five characteristics of the fifth generation computers. (5 marks)
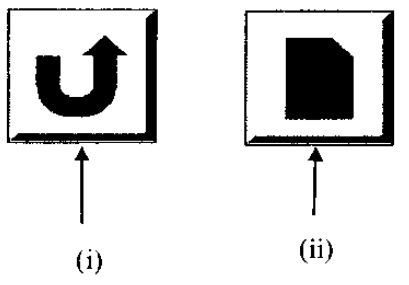
(c) Explain the function of each of the following tools labelled (i) and (ii) used in a presentation program. (4 marks)